Master of Science in Digital Forensics & Incident Response
School of Cybersecurity and Digital Sciences
Now Accepting ApplicationsProgram Overview
The Master of Science in Digital Forensics & Incident Response (MS DFIR) prepares students to investigate, analyze, and communicate digital evidence in criminal, civil, corporate, and incident response contexts. The program emphasizes forensic soundness, investigative reasoning, legal defensibility, and professional communication over tool-centric or checklist-based training. Students gain hands-on experience using realistic, instructor-designed datasets while learning to reason under uncertainty, validate findings, and clearly articulate limitations. The curriculum balances approximately 70% technical content with 30% legal, ethical, and investigative instruction and culminates in a comprehensive capstone investigation.
Program Highlights
- Reasoning-first curriculum emphasizing defensible forensic methodology
- Fully online, asynchronous format designed for working professionals
- Hands-on labs using shared, longitudinal forensic datasets
- Writing-intensive forensic reporting and scenario-based exams
- Summative capstone investigation integrating all program learning outcomes
- Alignment with major digital forensics and DFIR certification domains
Program Structure
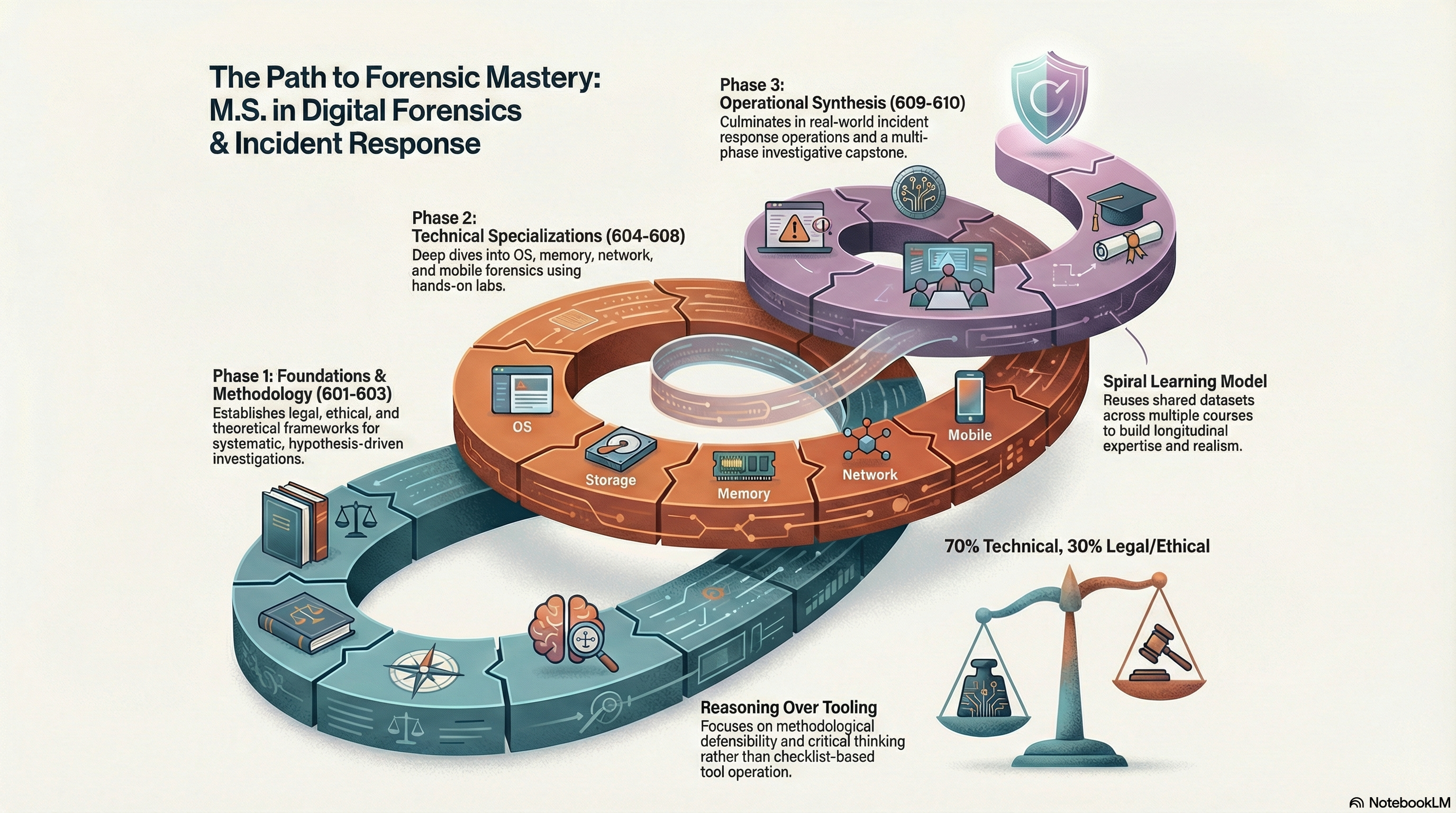
Curriculum
Core Courses (10 courses)
Foundations of Digital Forensics
3 creditsIntroduces digital forensics as a technical, investigative, and professional discipline, emphasizing forensic principles, evidence lifecycles, and hypothesis-driven reasoning.
Legal, Ethical, and Professional Issues in Digital Forensics
3 creditsExamines legal frameworks, evidentiary standards, professional ethics, and expert witness responsibilities governing digital forensic practice.
Digital Investigation Theory & Methodology
3 creditsFocuses on investigative models, hypothesis formulation, bias mitigation, documentation, and defensible forensic decision-making.
Operating System & File System Forensics
3 creditsDevelops proficiency in interpreting OS and file system artifacts to reconstruct user and system activity in a forensically sound manner.
Disk, Storage, and Data Acquisition
3 creditsExplores principles and practices of digital evidence acquisition, emphasizing validation, documentation, and defensibility of acquisition choices.
Memory, Malware, and Program Execution Forensics
3 creditsFocuses on volatile memory, malware behavior, and execution artifacts, emphasizing interpretation under uncertainty and corroboration across sources.
Network & Cloud Forensics
3 creditsExamines forensic analysis of network traffic, logs, and cloud artifacts, emphasizing distributed event reconstruction and evidentiary scope.
Mobile, IoT, and Embedded Device Forensics
3 creditsAddresses forensic investigation of mobile, IoT, and embedded systems, focusing on data provenance, acquisition feasibility, privacy, and limitations.
Digital Forensics in Incident Response
3 creditsIntegrates digital forensics into incident response operations, emphasizing forensic triage, evidence preservation, and decision-making under operational constraints.
Digital Forensics Capstone
3 creditsA summative, multi-phase forensic investigation requiring students to synthesize technical analysis, investigative methodology, legal compliance, and professional reporting.
Career Outcomes
- Digital Forensic Examiner
- DFIR Analyst
- Incident Response Analyst
- Cyber Investigations Analyst
- eDiscovery or Corporate Investigations Specialist
Program Learning Outcomes
Upon successful completion of this program, graduates will be able to:
- Apply forensically sound processes to acquire, preserve, analyze, and present digital evidence
- Design and conduct systematic, hypothesis-driven digital investigations
- Analyze digital artifacts across operating systems, storage, memory, networks, cloud, and mobile platforms
- Evaluate forensic tools and techniques with respect to accuracy, limitations, and error
- Integrate legal, ethical, and professional standards into forensic and incident response activities
- Communicate technical findings clearly to technical, legal, and executive audiences
- Function effectively on multidisciplinary investigative and incident response teams
- Engage in continuous professional development and ethical practice
Assessment Model
Assessment emphasizes professional reasoning, methodological defensibility, and communication rather than memorization or tool command recall.
Assessment Methods
- Reasoning-focused exams
- Hands-on forensic laboratories
- Writing-intensive forensic reports
- Scenario-based analysis projects
- Summative capstone investigation
Certification Alignment
The program is not a certification bootcamp. Curriculum content aligns conceptually with major digital forensics and DFIR certification domains and supports informed pursuit of certifications when combined with professional experience.
Aligned Certifications
- GIAC Certified Forensic Examiner (GCFE)
- GIAC Certified Forensic Analyst (GCFA)
- Certified Forensic Computer Examiner (CFCE)
- EnCase Certified Examiner (EnCE)
Program Delivery
- Asynchronous online courses
- Instructor-designed, authorized forensic datasets
- Standardized program-wide assessment rubrics
- Designed to meet ABET-style outcomes assessment expectations
Admission Requirements
Required
- Bachelor's degree from an accredited institution
- Foundational knowledge of operating systems, networking, and computing concepts
- Minimum 3.0 GPA (or demonstrated professional experience)
- Statement of purpose
- Resume or CV
Preferred Qualifications
- Background in IT, cybersecurity, computer science, law enforcement, or related fields
- Professional experience in security, investigations, or technical roles